$3.1 Billion Lost: Crypto Security Under Siege in H1 2025, Hacken Reports

Hacken’s “Half Year Web3 Security Report” reveals an unprecedented scale of Web3 losses in H1 2025, with $3.1 billion stolen – surpassing all of 2024’s total. This data underscores the critical need to rethink cybersecurity approaches, as malicious actors increasingly exploit not only technical vulnerabilities but also the human element.
The $3.1 Billion Breakdown: Where Web3 Lost Money
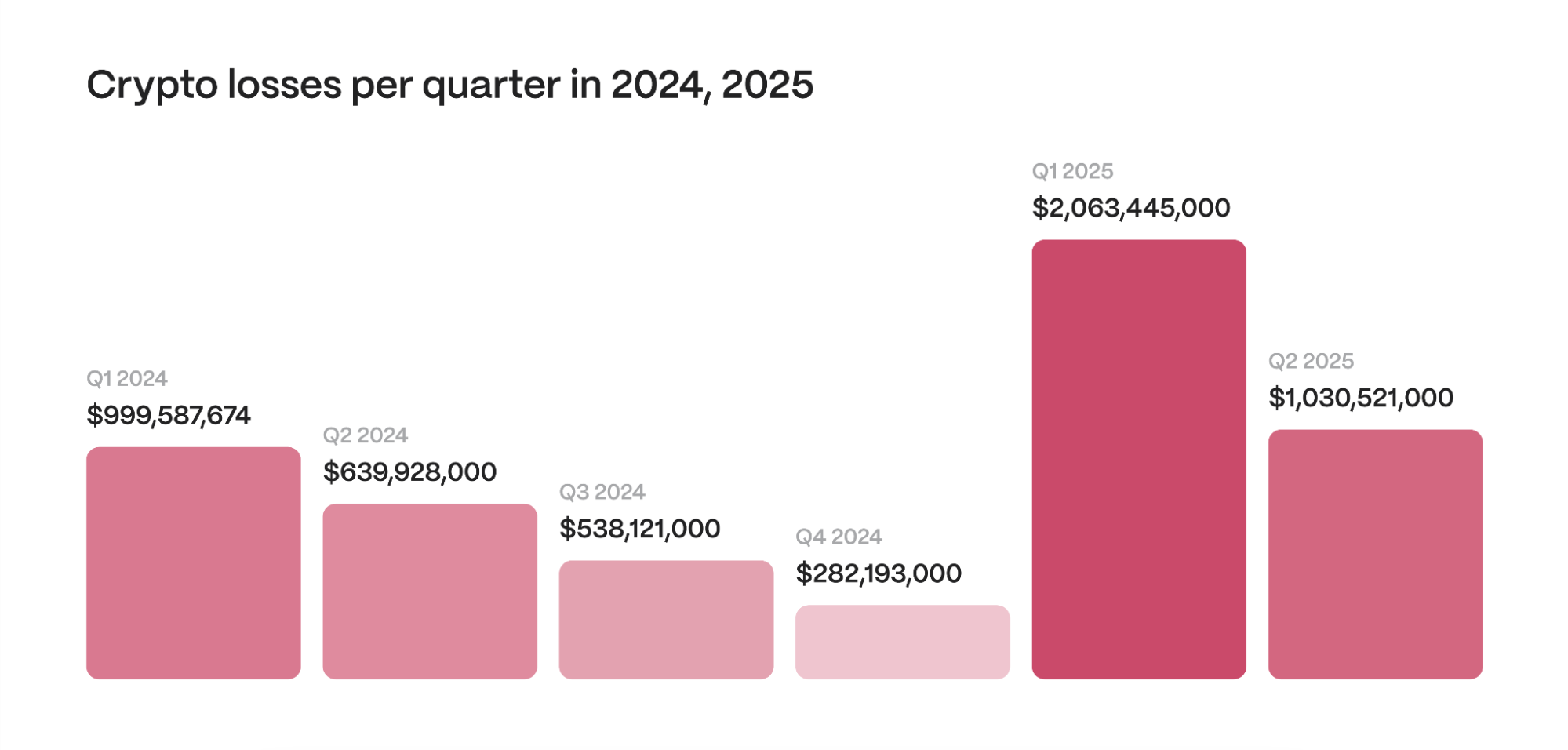
The numbers tell a disturbing story: $3.1 billion stolen in six months versus $2.85 billion for all of 2024. Hackers have cracked the code on something much simpler than breaking smart contracts – they’re breaking human psychology instead.
The first quarter of 2025 was particularly alarming, with $2.06 billion lost, while the second quarter saw losses of $1.03 billion. The DeFi sector experienced its worst quarter since 2023, and the Uniswap V4 exploit, which led to $12 million in losses for Cork Protocol, marked the first major breach in this new version.
Attack Vectors: How Hackers Strike
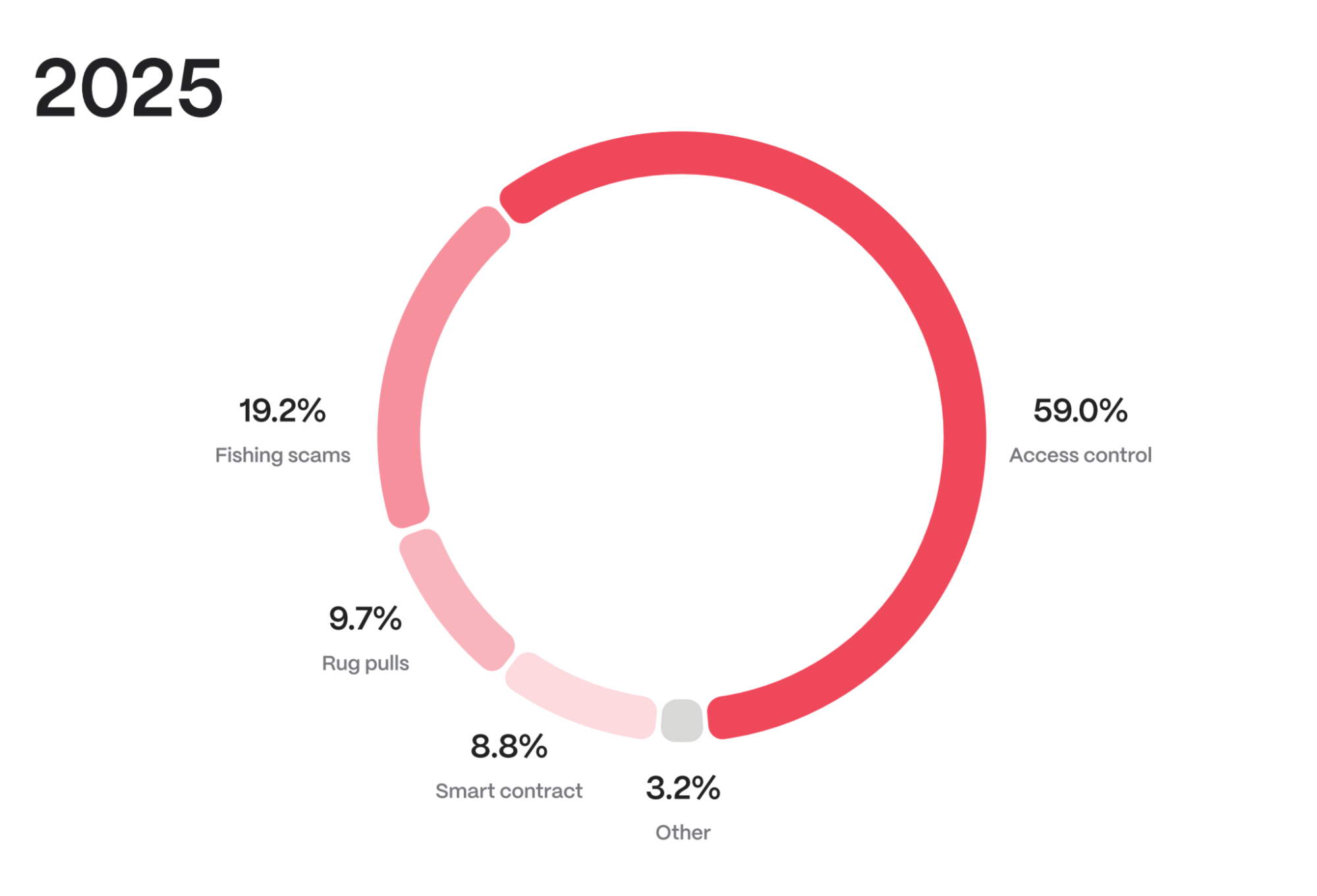
An analysis of losses by attack type reveals the dominant threat vectors:
- Access Control Exploits: $1,826,493,000 (approximately 59% of total losses). This type of attack, targeting compromised accounts and keys, proved to be the most destructive.
- Phishing Scams and Social Engineering: $594,170,000 (≈19%). These methods, based on manipulating users, continue to incur significant losses.
- Smart Contract Vulnerabilities: $273,183,000 (approximately 8%). Despite a smaller share, individual incidents, such as the Cetus hack, were extremely costly.
- Rug Pulls: $300,100,000. Fraudulent projects that suddenly disappear with user assets remain a serious problem.
- Other: $99,999,000. This category includes various less common, but still significant, types of attacks (e.g., exploits discovered long after deployment, as in the case of 1inch’s Settlement).
Major 2025 Security Incidents:
- Bybit Compromise: nearly $1.5 billion lost due to compromised signer interface.
- Nobitex Exchange: $90 million stolen from Iran’s largest crypto exchange
- UPCX Attack: $70 million drained through hijacked ProxyAdmin account
- Individual Bitcoin Theft: $330 million stolen from elderly U.S. citizen via phishing
From Code Exploits to Human Psychology
The Hacken report highlights a disturbing trend: attackers are increasingly shifting their focus from purely technical vulnerabilities to human and organizational procedures. Compromised access control has become the dominant attack vector, indicating a lack of operational security maturity in the Web3 space. This includes blind signing attacks, private key leaks, and sophisticated phishing campaigns.
Examples of such attacks are numerous and diverse. In addition to the aforementioned Bybit hack, where a Safe Wallet was compromised, other significant incidents occurred. For instance, Infini Protocol lost $50 million when a former developer simply withdrew all funds. On UPCX, attackers hijacked the ProxyAdmin account, pushed through a malicious upgrade, and drained tokens worth approximately $70 million. In the KiloEx case, a missing permission check allowed manipulation of oracle prices, leading to $7.5 million in losses.
Even attacks like the backdoor planted by a developer in the Roar contract resulted in $800,000 in losses. The compromise of a zkSync admin key, which turned out to be a 1-of-1 multisig, allowed the withdrawal of about $5 million in unclaimed ZK airdrop tokens. The attack on Iran’s largest crypto exchange, Nobitex, on June 18, 2025, led to the theft of over $90 million in various assets.
Phishing scams and social engineering also reached new record highs. The largest theft from a single individual amounted to $330 million in Bitcoin, when an elderly U.S. citizen was tricked into handing over wallet access. Coinbase users also suffered from phishing and vishing after a data breach, with scammers posing as support staff extorting over $100 million. These incidents demonstrate that even with perfectly functioning cryptography, billions of dollars can be lost due to weak human and procedural controls. Hacken experts emphasize that this is a systemic issue, not merely a user problem.
The New Frontier for Cyber Attacks
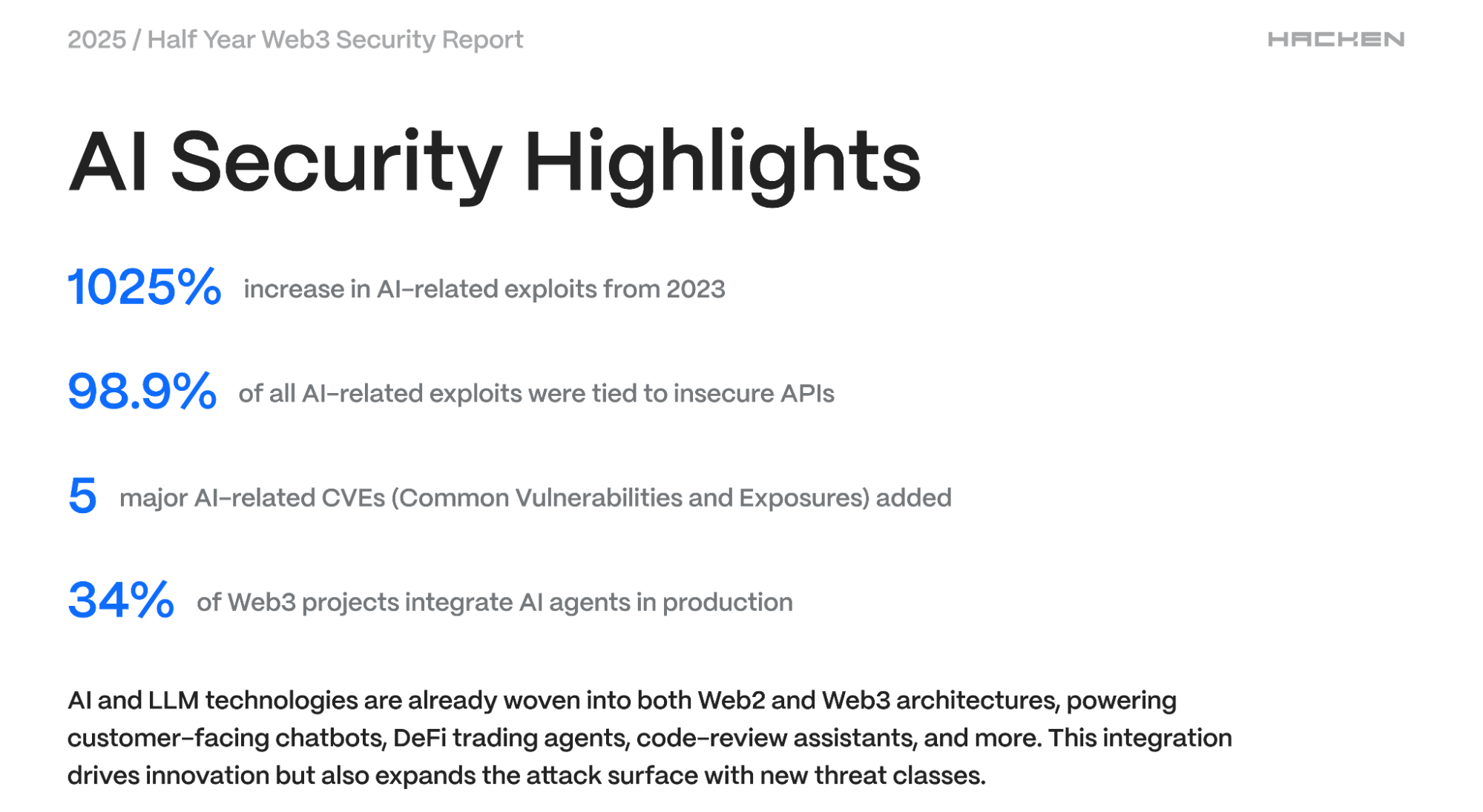
The integration of artificial intelligence and large language models (LLMs) into Web2 and Web3 architectures, from customer-facing chatbots to DeFi trading agents and code-review assistants, opens new opportunities but also significantly expands the attack surface. The Hacken report notes a 1025% increase in AI-related exploits since 2023, with 98.9% of them linked to insecure APIs. Approximately 34% of Web3 projects already use AI agents in production, making this area critically important for security.
Key AI system security risks include: prompt injection (where malicious inputs override LLM instructions), training data poisoning (subtle corruption of data to create backdoors), model theft and inference attacks (reconstruction of proprietary model parameters), supply chain compromises (malicious dependencies in ML frameworks), and agentic AI exploits (vulnerabilities in multi-agent systems).
2025’s Most Devastating AI Security Breaches
A series of high-profile incidents in 2025 demonstrated the severity of AI-related threats:
- Langflow RCE (CVE-2025-3248). A critical, unauthenticated code injection flaw in Langflow’s code-validation API, actively exploited across ~1,050 exposed instances worldwide.
- BentoML Deserialization (CVE-2025-32375). Insecure deserialization in BentoML allowed arbitrary code execution via crafted headers.
- Drupal AI Command Injection (CVE-2025-31692). OS command injection in Drupal’s AI module enabled unauthorized system commands.
- MITRE Caldera RCE (CVE-2025-27364). A zero-day in the adversary-emulation tool allowed remote code execution during agent compilation.
- Prompt Injection on Commercial LLMs. Researchers exploited hidden instructions to corrupt long-term memory in Google Gemini and other models, demonstrating persistent manipulation risks.
- “Vibe Hacking”. “Vibe hacking” kits, such as WormGPT, enable non-expert actors to generate sophisticated exploits, lowering the barrier for large-scale malware campaigns.
In response to these threats, Hacken proposes a series of key mitigations for AI risk, including adversarial testing, pipeline hardening, supply chain hygiene, the use of Model Context Protocols (MCP), runtime monitoring and explainability, as well as regular training and awareness for teams.
As Stephen Ajayi, DApp Audit Technical Lead at Hacken, notes: “The promise of AI is massive, but so are the risks. By addressing AI-specific threats and embedding security throughout the AI lifecycle, businesses can innovate with confidence. Our AI System Security Audit helps teams build LLMs, agentic AI, and generative systems on strong security foundations from day one.”
What This Means for Web3’s Future
The $3.1 billion in losses during H1 2025 represents more than just numbers—it signals a fundamental shift in how attackers target blockchain systems. With 59% of losses coming from access control failures rather than smart contract bugs, the industry must prioritize human-centered security training, multi-signature governance, and AI-resistant authentication systems.
Organizations serious about Web3 security must implement comprehensive auditing, employee training programs, and emerging AI security frameworks. As Stephen Ajayi from Hacken warns: “The promise of AI is massive, but so are the risks.” The question isn’t whether your organization will face these threats—it’s whether you’ll be prepared when they arrive.
Content on BlockPort is provided for informational purposes only and does not constitute financial guidance.
We strive to ensure the accuracy and relevance of the information we share, but we do not guarantee that all content is complete, error-free, or up to date. BlockPort disclaims any liability for losses, mistakes, or actions taken based on the material found on this site.
Always conduct your own research before making financial decisions and consider consulting with a licensed advisor.
For further details, please review our Terms of Use, Privacy Policy, and Disclaimer.



























