Fake CAPTCHA attacks put crypto wallets at risk through Lumma Stealer malware

Fake CAPTCHAs look like familiar security checks but actually lead to cryptocurrency theft. We explain the attack mechanics, how Lumma Stealer works, and protection strategies.
On this page
- Fake CAPTCHA pages disguise malware delivery by exploiting user trust
- Lumma Stealer malware targets passwords, crypto wallets, and 2FA data
- Malware-As-A-Service model makes attacks cheaper and more sustainable
- Practical Steps To Avoid Falling Victim To Fake CAPTCHA And Wallet Theft
- Staying ahead of evolving crypto threats
Fake CAPTCHAs disguised as the familiar “I’m not a robot” verification have become cybercriminals’ newest weapon. Users think they’re simply confirming their identity, but they’re actually triggering malware installation. This approach works particularly well because users have trusted CAPTCHA interfaces for years and rarely raises suspicion today.
Recent research reveals that Lumma Stealer – one of the most aggressive info-stealers targeting passwords, crypto wallets, and two-factor authentication tokens – powers this scheme. The scale of the problem shows we’re not dealing with isolated attacks, but an entire business model where malicious code is sold as a subscription service.
Fake CAPTCHA pages disguise malware delivery by exploiting user trust
Fake CAPTCHA pages exploit user trust in the familiar “I’m not a robot” verification. At first glance, they look like standard verification windows, but instead of confirming user identity, they trigger a chain of actions leading to malware installation on the target device. Since CAPTCHAs are associated with security, most people don’t suspect foul play, making such attacks particularly effective.
In one real case, a fake CAPTCHA was embedded on a banking website that asked users to copy and paste code into the Windows Run dialog. Despite the obviously suspicious request, some visitors followed the instructions and triggered the infection process.
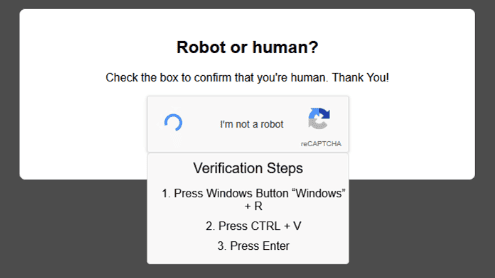
Within just a few days, the system recorded dozens of interactions, with nearly one in five users falling victim to this scheme.
The danger intensifies because attacks can appear on legitimate websites too. Criminals exploit vulnerabilities or inject malicious scripts, turning even trusted resources into threat sources. To boost credibility, criminals register new domains and pages that visually copy Google reCAPTCHA’s interface, further reducing user suspicion.
Lumma Stealer malware targets passwords, crypto wallets, and 2FA data
Lumma Stealer ranks among the most prominent info-stealers of recent years. Once it infiltrates a system, it immediately begins collecting data. It primarily targets browser-saved passwords, cookies, two-factor authentication tokens, and crypto wallet data.
Unlike traditional viruses, Lumma spreads as a fileless threat, meaning it can operate without installing visible files, significantly complicating detection by standard antivirus software.
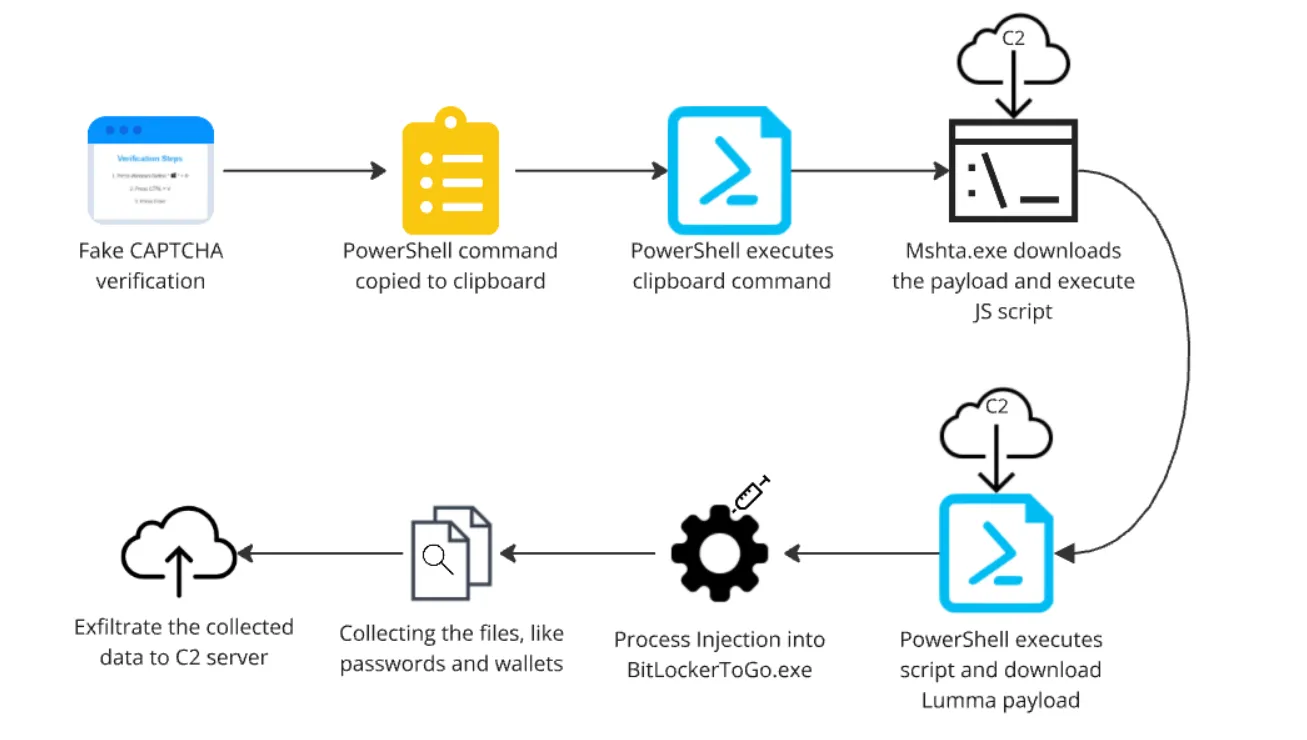
For cryptocurrency users, risks are particularly high. Losing seed phrases or private keys leads to direct asset theft – unlike conventional services, there’s no account recovery or fund retrieval function. Even a single infection can mean instant loss of savings.
Moreover, Lumma Stealer can search for data in less obvious places, such as password managers or remote access configurations.
The danger escalates because stolen data rarely stays in one place. Most often, it’s passed to “traffic teams” that specialize in reselling and mass-using stolen credentials. As a result, one attack becomes an entire cascade of threats: from simple personal email hacks to cryptocurrency theft and full-scale digital identity fraud.
Malware-As-A-Service model makes attacks cheaper and more sustainable
Lumma Stealer exemplifies how cybercrime is becoming a business with stable revenue models. This malicious code is distributed by subscription – starting at just $250 per month – making it accessible even to novice cybercriminals. Instead of spending resources developing their own code, criminals can simply “rent” a ready-made solution and immediately begin attacks.
This approach ensures sustainability and scalability. Lumma Stealer developers regularly update functionality, improve antivirus evasion methods, and register new distribution domains. Essentially, operators run a business where customers are criminals and the product is a ready-made data theft tool.
The numbers are staggering: in 2023, cumulative losses from Lumma Stealer usage were estimated in tens of millions of dollars, with infected device counts exceeding hundreds of thousands. Even large-scale law enforcement actions that shut down thousands of malicious domains don’t completely destroy the network. New infrastructure appears almost immediately, turning the fight against MaaS into a long-term struggle.
This model shows that cyber threats are no longer isolated incidents. Today, it’s an entire industry operating on the same principles as legitimate SaaS companies: regular updates, customer support, and continuous product improvement.
Practical Steps To Avoid Falling Victim To Fake CAPTCHA And Wallet Theft
Protection against fake CAPTCHA attacks requires combining technical measures with careful user behavior. Criminals increasingly use social engineering methods, disguising malicious actions as familiar interfaces. Therefore, any unexpected instruction, especially involving manual command entry, should raise suspicion.
The first protection level involves checking the domain and SSL certificate. Even if a page looks familiar, it’s important to verify that the address matches the official one and the connection is secure. The second rule: never follow instructions that involve copying and pasting code from browsers into system utilities. This is a key social engineering indicator.
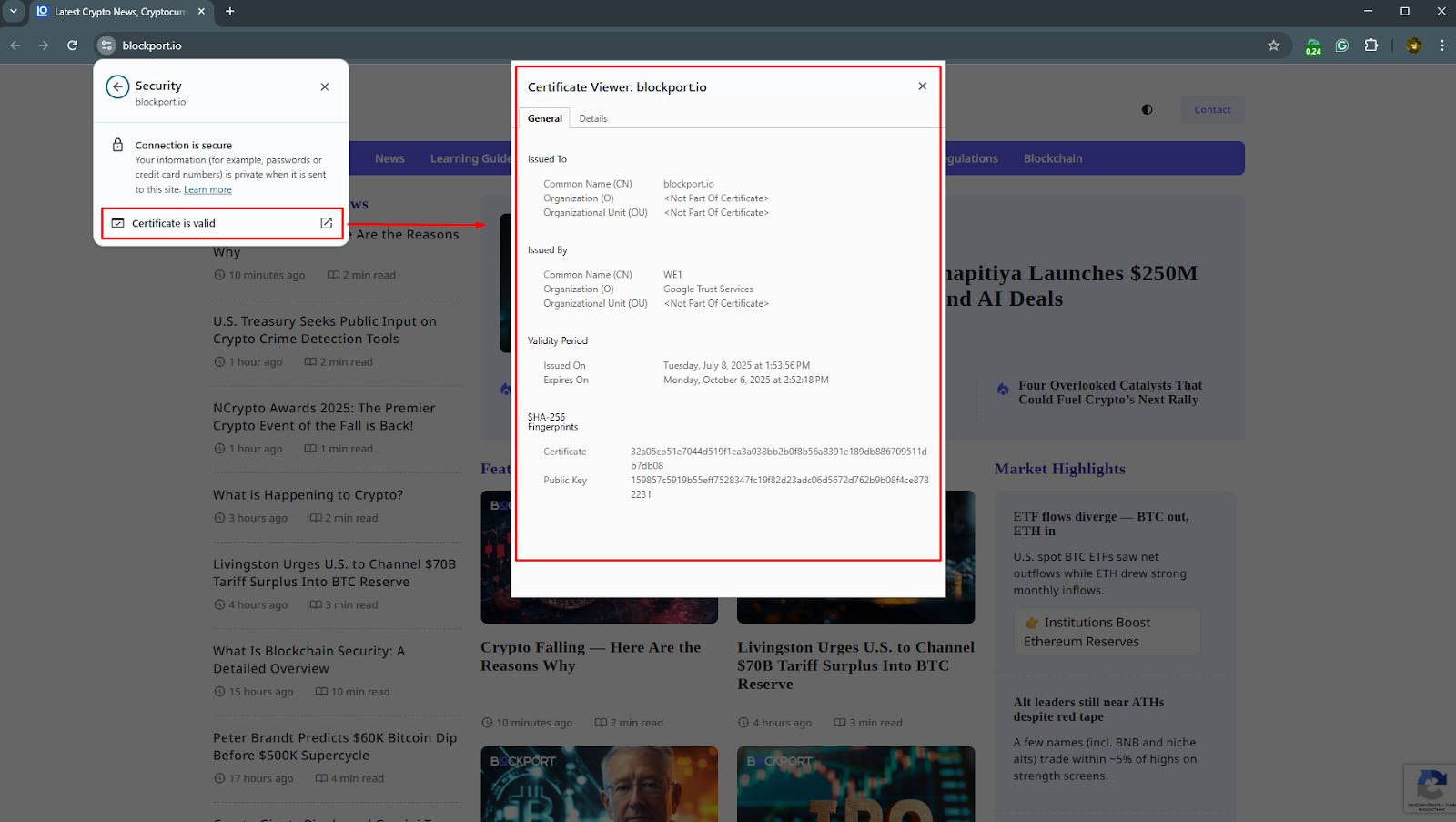
On the technical level, protective DNS systems and content filtering are recommended. These solutions block suspicious domains before users can reach them, reducing infection risk. For cryptocurrency holders, cold wallets and backup seed phrase storage should serve as additional defense lines, preventing direct theft if devices become infected.
Organizational-level prevention is equally important. Regular employee training on cybersecurity best practices reduces error rates and lowers successful attack probability. Since humans remain the weakest link, they need constant attention and systematic approaches.
Staying ahead of evolving crypto threats
Fake CAPTCHAs demonstrate how ingeniously cybercriminals exploit user trust in familiar security elements. A simple “I’m not a robot” checkbox becomes a tool launching complex attacks and leading to valuable data and cryptocurrency asset theft.
The danger of such schemes lies not only in the malware’s technical capabilities but also in humans remaining the weakest security link. This is why protection must include both modern technical solutions and constant attention to cyber hygiene – only this combination can reduce digital asset loss risks.
Content on BlockPort is provided for informational purposes only and does not constitute financial guidance.
We strive to ensure the accuracy and relevance of the information we share, but we do not guarantee that all content is complete, error-free, or up to date. BlockPort disclaims any liability for losses, mistakes, or actions taken based on the material found on this site.
Always conduct your own research before making financial decisions and consider consulting with a licensed advisor.
For further details, please review our Terms of Use, Privacy Policy, and Disclaimer.

























